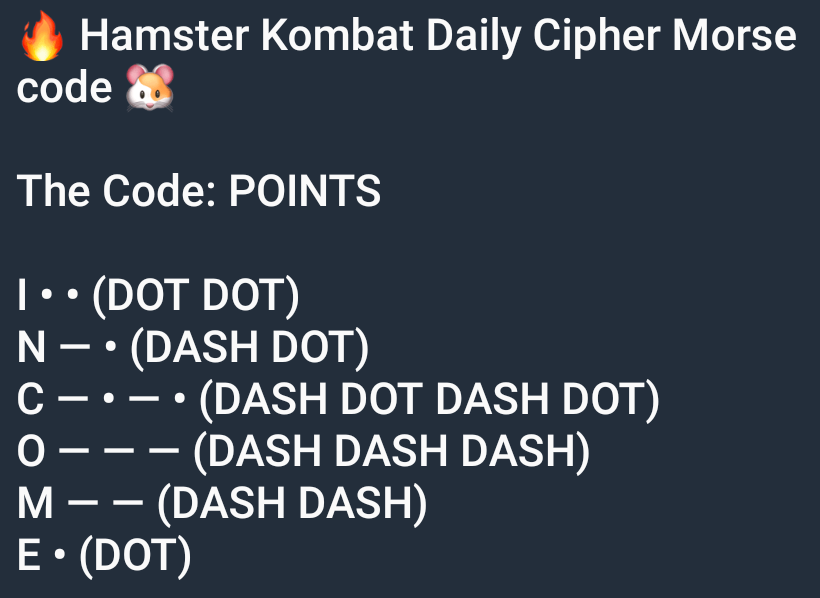
Hamster Kombat Daily Cipher code 14 August 2024
Understanding Hamster Combat Cypher Code: A Comprehensive Overview
In the realm of cryptography and puzzle-solving, the Hamster Combat Cypher Code stands out as a fascinating example of creative encryption. This code, named whimsically after hamsters and combat, combines elements of traditional cipher techniques with unique twists that make it both challenging and engaging.
Origins and Purpose
The Hamster Combat Cypher Code is a product of contemporary cryptographic experimentation, designed to intrigue both amateur and experienced cryptographers. It emerged from a desire to create a cipher that balances complexity with accessibility, allowing enthusiasts to explore encryption techniques in a playful yet intellectually stimulating way.
Mechanics of the Cipher
At its core, the Hamster Combat Cypher Code operates on principles similar to classical ciphers but introduces distinctive features. The cipher typically uses a substitution method where each letter of the plaintext is replaced by a different letter according to a specific algorithm. The key to the code is its unique substitution rules, which can involve various transformations, such as:
Pattern-Based Substitution: Instead of straightforward letter replacement, the cipher employs patterns derived from various sources, such as animal behavior or combat strategies, to determine the substitutions.
Multiple Shifts: The code may incorporate multiple shifting techniques where the number of positions each letter is shifted varies according to predefined sequences or randomization.
Layered Encryption: In more advanced versions, the cipher includes multiple layers of encryption. Each layer applies a different substitution method or mathematical transformation, adding to the complexity of decoding.
Decoding the Cipher
Decoding the Hamster Combat Cypher Code involves reverse-engineering the encryption process. To decrypt a message, one needs to understand the specific substitution rules used during encryption. This typically requires knowledge of the cipher’s key or pattern, which can be discovered through various cryptographic techniques, such as frequency analysis or pattern recognition.
Frequency Analysis: By analyzing the frequency of letters or patterns in the ciphertext, one can make educated guesses about the substitutions used.
Pattern Recognition: Identifying recurring patterns or sequences can provide clues about the substitution rules and help in reconstructing the plaintext.
Brute Force: In cases where the cipher is complex, a brute-force approach, trying all possible combinations until the correct one is found, may be necessary.
Applications and Challenges
The Hamster Combat Cypher Code is primarily used for educational and recreational purposes. It serves as a tool for learning about encryption techniques and improving problem-solving skills. However, its playful nature and complexity also present challenges, making it a popular choice for cryptographic competitions and puzzles.
Conclusion
The Hamster Combat Cypher Code exemplifies how traditional cryptographic methods can be adapted to create engaging and challenging puzzles. Its blend of familiar encryption techniques with unique, creative elements makes it a valuable tool for both learning and entertainment. As with any cryptographic method, understanding its mechanics and mastering the techniques requires practice and patience, offering both a rewarding and enjoyable experience for those who take on the challenge.